A Sidenote and an Additional Dislaimer. First, the sidenote. This diary grew out a stream-of-consciousness comment in Soj's JPEN diary, currently on the Daily Kos recommended list. The additional disclaimer is that I am going to explain this by use of a scenario. The scenario has evolved over years of technology companies working with investigative and intelligence agencies. In short, a technology company will proffer a "likely application" of their technology that fits the mission of the agency or entity on whome they are calling. It is not a case of a government entity coming to a technology company and saying "What if I wanted to do [insert scary thing here]?" I do not know for a fact that this technology is being used, but I know that the capability is being sold.Now to the scenario.
Let's say that a large wire transfer is made from a bank in Saudia Arabia to four separate banks in the US. The US banks are in San Francisco, New York, Miami and Washington, DC. The foreign bank is being surveilled electronically and it is that surveillance which captures the transaction. At this point the intelligence unit knows only that a foreign bank it considers suspect has made a wire transfer of a sufficiently large sum of money to domestic financial institutions. They don't know who made the transfer and they don't know who owns the US accounts where the monies were deposited.
They go and get a warrant to compel the bank to disclose information on the account holders. This may be very basic information - for our purposes, let's say that it's the name and address listed for each of the four accounts and that each recipient is a different person with a different name and address. The intelligence unit then sends the names and addresses gleaned from the warrant to another intelligence unit who maintains a central terrorist screening database. The individuals at the terrorist screening database who receive the request to run the names are not told why they are running the names. They are only to report whether or not the names (normalized to allow for common misspellings and differences in linguistics) occur in their database. In essence, they are returning a "true" or "false" answer to the original intelligence unit - "true" if the name occurs, "false" if it doesn't. For the sake of this scenario, the results of all four names are "false".
But it doesn't end there.
The original intelligence unit has reason to believe that the foreign bank has initiated transactions that are suspect in nature in the past and that the current transactions are so sizeable that they necessitate additional investigation. Having the names and addresses of the US account holders, they use a visualization application to perform link analysis. Link analysis is exactly that - it is a visual software toolset that depicts relationships between persons, known and unknown. Stepping away from our scenario, here's a sample screenshot of such a link analysis tool:
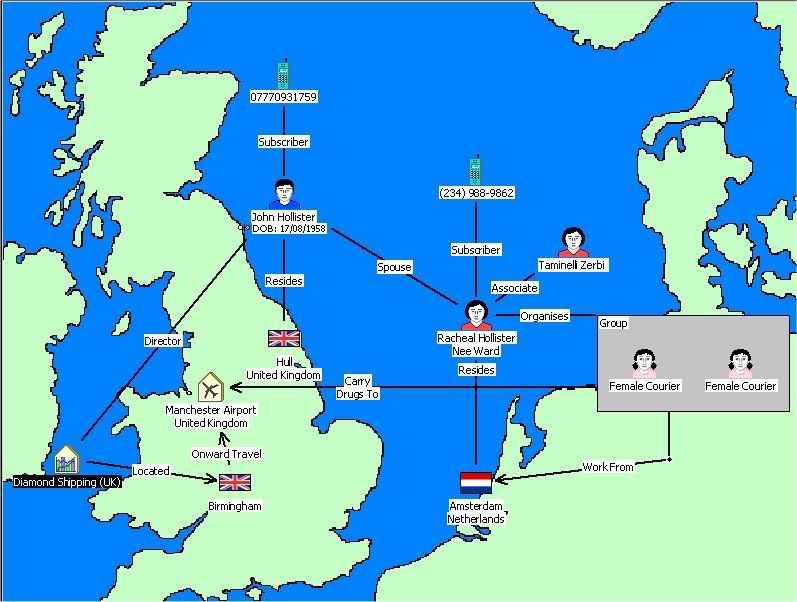
(You can link to a larger picture here)
Note the different representations and icons for persons and links. This is a powerful investigative and analytical tool for enforcement and intelligence analysts. It allows them to "see" a network of persons, companies, countries, accounts, etc.
Now back to the scenario. Right now, the links in the software are between the four individuals, their domestic financial institutions, and the original foreign bank. In short, it's a pretty elaborate depiction of the wire transfer without any specific information as to nature of the recipients. On its own, it doesn't give the analyst much information that wasn't already known.
Enter, then, what I will refer to as the information repositories. Let's say that I wanted to take the name and address of one of the US funds recipients and determine who their "known associates" are. Let's say further that there is a company out there that specializes in collecting information about people. Some of that information is public, some of it isn't.
Stepping outside of the scenario, think of this capability in a very personal way. If I were to take your name and street address and plug it into an application that quickly spidered publicly available data sources, what information would I get back? Well, first, I would get all the information about your home, what you paid for it, when you bought it, where it is, who the neighbors are, what they paid for it, who (if anyone) is listed as a director of your homeowner's association, whether or not you have any records in the criminal, civil and/or appellate court systems, whether or not you have judgments against you and liens against your property, etc. and so forth. In short, I could find out a lot about you simply by bringing together in one place a way to index and search these publicly available data sources.
Now back to the scenario. I want to know more about each of these four funds recipients. I can spider not only public data sources but also government-held data sources. I can get a picture of their income, employment, what they own, what charities they donate to, what they owe, who their neighbors are, who their co-workers are, who their children and spouse are, who they associate with, etc. I'm starting to fill in the blanks.
Let's say that one of the individuals I'm investigating is a male named John Doe. Through use of the information repositories and the application technology they offer, I know that John Doe gives money regularly to a mosque where he worship. I also learn that YOU, the reader, are a neighbor of John Doe. Not only that - John Doe, in trying to give the appearance of being an upstanding citizen, sits as the Treasurer of your homeowner's association, of which you are President. John Doe is a local business owner - he owns a home improvement contracting company - and you, the reader, being a good neighbor, have used John Doe and have paid him to do work on your home. The investigating agency knows this because John Doe has declared what you paid him as income and a check from you has been deposited, at some point in the past, in John Doe's account.
The same account to which John Doe received the wire transfer of funds from the foreign bank, the very transaction which started the whole process.
YOU are now added as a link to John Doe in the analyst's link analysis software tool. All of this information as well as information from other strong known associates of John Doe is used to apply to FISA to put you under surveillance.
Seem far-fetched? It isn't. Let me say for the record that many of these technologies and tools are invaluable in doing legitimate investigative work. Their existence pre-dates by far the 9/11 attacks. Picture a crime syndicate and the power of such a tool in unravelling all of the tendrils - hell - picture the value of such a tool in mapping the Abramoff investigation. So I'm saying that the tools themselves are not bad.
What is bad is the existance of these tools in today's intelligence climate. As far as I know, nothing that I laid out in my scenario involved an instance of illegal surveillance. I can't even envision the scenario that would develop when I consider illegal wiretapping.
The only thing that protects you from being involved in a scenario like this is some degree of transparency in the law enforcement and intelligence arenas and a DEMAND that governmental entities follow the letter of the law when it comes to surveillance of private citizens.
Big brother is a series of 0's and 1's and is, for all intents and purposes, the very means by which I am communicating with you today.
How's that for alarming?














1 Comments:
Off topic, but I'm notifying you that you have been tagged. No, not by the governmnet (hahaa) but by a bunch of loony leftie bloggers.
See my blog Moondancer for the jist of it. You may blame Carnacki for all of it!
Great diary Rena, as usual! - CD
Post a Comment
<< Home